PBS v2 (Beta Search) | Public Breached Search V2
Overview of the Service
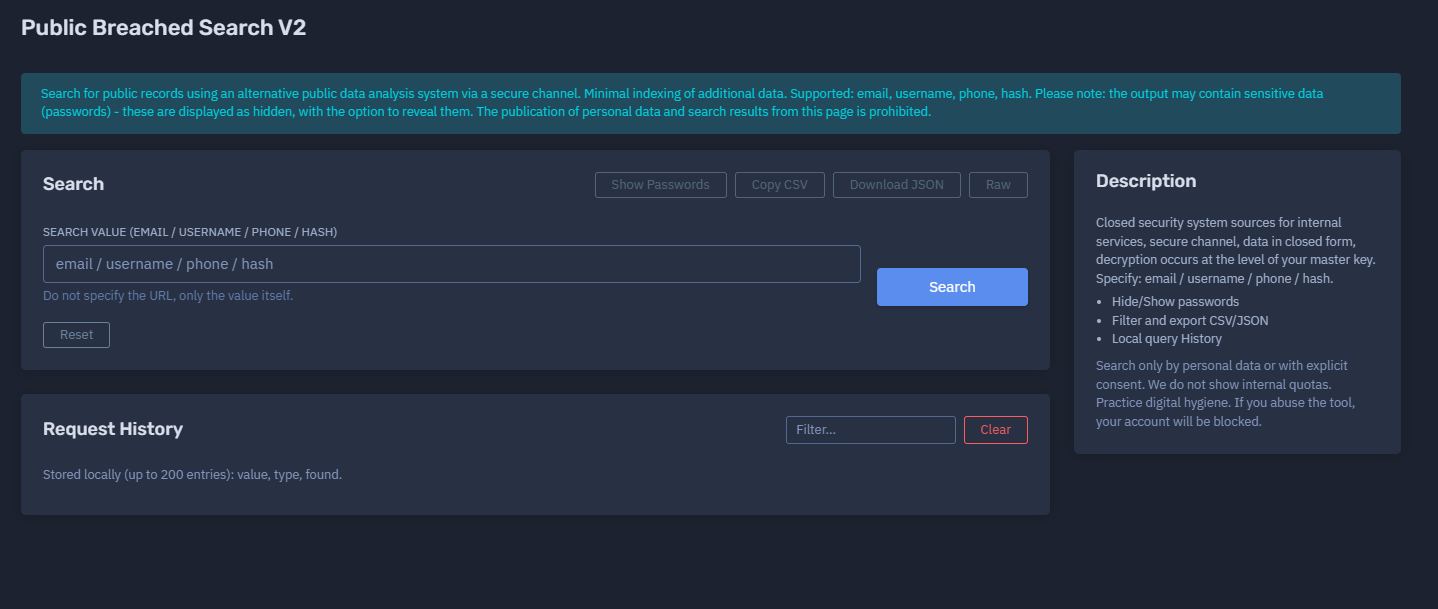
The platform available at dash.niamonx.io/breaches_s_v2 — known as Public Breached Search V2 — is an advanced, security-focused version of the NiamonX breach intelligence engine.
It enables users to safely and privately search for publicly available leaked records (emails, usernames, phone numbers, or hashes) through a fully encrypted channel, using an enhanced privacy-preserving architecture.
This system is designed for individuals, analysts, and cybersecurity teams who need to verify whether specific identifiers have been compromised — without exposing their search queries or retrieved data.
🔍 How the Search Works
When a user submits a query — such as an email address, username, phone number, or hash — the system performs a real-time lookup across an alternative, minimized index of public breach data.
The search is executed through a closed security network using end-to-end encryption and a master key–based decryption layer. This ensures that:
-
All transmitted data remains encrypted at every step.
-
Decryption occurs only on the client side, not on NiamonX servers.
-
The system never stores sensitive results or full identifiers in plain form.
This approach provides maximum privacy, ensuring that no third party — including NiamonX infrastructure — can access raw search data or results.
🧩 What Can Be Searched
Supported input types:
-
Email address
-
Username / Login
-
Phone number (international format)
-
Hash (MD5 / SHA1 / SHA256 and similar)
Unlike the standard Breached Search engine, V2 does not support URLs, domains, or combined queries. It focuses exclusively on personal identifiers and cryptographic hashes to maintain precision and data hygiene.
Passwords found in results are hidden (masked) by default. Users may reveal them manually if needed for verification, but they must not redistribute or publicly display that information.
🧠 Key Features
-
Encrypted Communication Channel: every search request and response is transmitted securely.
-
Client-side Decryption: sensitive content is decrypted locally using the user’s master key.
-
Minimal Indexing: only essential metadata is stored to ensure fast lookups while reducing exposure.
-
Local Query History: recent searches (up to 200 entries) are stored locally in the browser, not on the server.
-
Flexible Export: results can be exported in CSV or JSON format, excluding confidential fields.
-
Password Visibility Control: toggle to hide or show masked password fields.
-
Filtering System: refine results by data type or source metadata.
🛡️ Security, Privacy & Ethics
The service is built with security-first architecture and strict privacy guarantees:
-
All communication is conducted through a secure, encrypted channel.
-
Data is stored and processed in a closed system environment.
-
No internal quotas or usage metrics are publicly displayed to prevent misuse.
-
Searches must only be performed on your own data or with explicit permission.
-
Abuse or attempts to deanonymize datasets will result in account termination.
-
Publication of personal or sensitive data retrieved from the system is strictly forbidden.
Users are strongly encouraged to practice digital hygiene — for example, by changing passwords, enabling MFA, and avoiding credential reuse.
⚙️ Technical Highlights
-
Alternative breach dataset with minimal indexing
-
Closed internal security infrastructure
-
End-to-end encryption with client-side decryption
-
Local storage of query history (no server retention)
-
Supports: email / username / phone / hash
-
Output masking for passwords and sensitive fields
-
CSV/JSON export with filtering tools
📬 Contact Information
For any technical, legal, or privacy-related inquiries, users can reach the NiamonX team directly via:
-
support @ niamonx.io — Technical Support
-
other @ niamonx.io — General Inquiries
-
takedown @ niamonx.io — Requests for Data Removal / Privacy Takedowns
-
legal @ niamonx.io — Legal or Compliance Matters
Alternative contact channel:
🔗 Helpdesk: https://support.niamonx.io/
In summary, NiamonX Public Breached Search V2 is a secure, privacy-preserving intelligence system that enables safe and encrypted lookup of breach data.
It prioritizes user confidentiality, cryptographic protection, and ethical operation, ensuring that every search remains private, traceable only to the authorized user, and never exposed beyond their secure session.